AK Vorrat critizises federal trojan horse – causes more problems than it could solve
The justice department is working on an above board regulation to legalize the so-called ‘Bundestrojaner’ (Federal Trojan). Minister of justice Brandstetter is doing the utmost to grace the planned surveillance software with a new name – yet software planted by officials on someone else’s computer to deliver data to them is and always will be what’s known as a Trojan horse. Whether its installation shall be permissible only on location and not just remotely, changes nothing. If the state is using espionage software against their own population, this is not merely problematic from a base right perspective, it also undermines the safety of all other users.
For the applications named by minister Brandstetter, such as WhatsApp or Skype, milder means such as surveillance via Lawful Intercept Interfaces is absolutely sufficient. Technically adept users can very easily recognize that spy software is leaking data from their computers and accordingly adapt their behavior. It cannot be ruled out, that software might be manipulated or will later receive new directives, which presents the utilization of surveillance results with great challenges. The AK Vorrat is summarizing the most important arguments against the announced regulation, aiming to start a broad debate on the subject as early as possible.
“Federal spy software is a very bad idea. When the state is drawing on the black market for security gaps, in order to monitor its own people, this doesn’t make any of us safer. The ministry of justice simply waited for the next horrible terror attack to present this legislation suggestion. One shouldn’t use a population’s fear to make politics”, says Thomas Lohninger, head of the AK Vorrat, to justice minister Brandstetter’s announcements. This week, a draft for the monitoring of internet telephony is to undergo inspection, designing also for spyware to be legally installed on target persons’ computers in the course of house searches.
Problems over a Trojan’s complete life circle
This regulation does not deal with any of the inherent problems with this kind of spyware. They start with the programming, spanning the deliberate exploitation of security gaps and their acquisition on the black market, to the impossibility to obfuscate the transmission of data through the Trojan right up to the question of admissibility of evidence which could be manipulated at any given time through technical interventions.
The AK Vorrat has condensed the most important arguments along the complete life cicle – from acquisition through installation up to surveillance and de-installation – in this comprehensive chart. “The announcements surrounding this piece of legislation alone suggest that this is nothing less than another attempt at stripping down people’s basic rights without achieving any adequate advantage for crime prevention, respectively the fight against crime. We will initiate a broad public debate and give reason a loud voice – as we did with ‘Vorratsdatenspeicherung’ and with the ‘Staatsschutzgesetz’” – says Christof Tschohl, chairman and lawyer to the AK Vorrat.
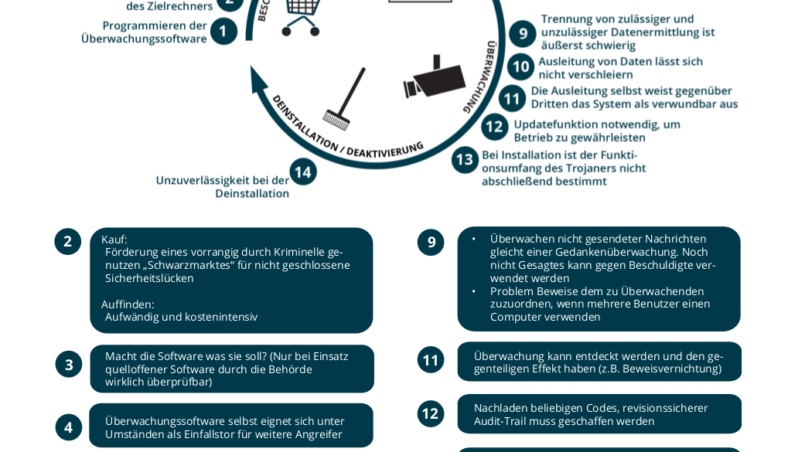
We are therefore calling on the ministry of justice to retract the legislation suggestion and utilize sufficient, more moderate means in Austria, instead of spy software.
Translation from German: Serena Nebo
Credits
| Image | Title | Author | License |
|---|---|---|---|
 |
Staatstrojaner Infografik | AK Vorrat | CC BY 4.0 |
